The Compilation of Many Breaches (COMB) has been published on a surface web hacking forum, making 3.2 billion pairs of passwords and emails easily searchable.
Since February of 2021, there has been much chatter on the surface and dark web (Tor specifically) concerning the Compilation of Many Breaches, affectionately referred to as “COMB.” The leaks are not necessarily new but a combination (as the name implies) of several breaches rolled into one convenient place.
The breach was published on a popular surface web hacking forum where 3.2 billion pairs of passwords and cleartext emails were published. Some of those affected by the 252 previous breaches and whose private data included in the rollup were Bitcoin, LinkedIn and Netflix, just to name a few.
To put 3.2 billion in perspective, consider the current world population is approximately 7.9 billion of which 4.7 billion are internet users in 2021.
Unfortunately, this is not the first time a COMB has occurred. In 2017, approximately 1.4 billion credentials were leaked in a similar manner.
To enable nefarious hackers to profit from the leak or for personal amusement, the cybercriminals behind or affiliated with COMB have made the data available on the surface web. A simple Google search will yield detailed information and resources on how to configure an environment to benefit from the stockpile of usernames and credentials.
Learn how to improve trust and safety investigations across the surface, deep and dark web while protecting investigators and their organizations >
For online investigators with access and experience searching the dark web, more COMB data and context is available there.
The following images were obtained from dark web forums. The dark web URLs and generic passwords are supplied to log into a database where the credentials were compressed (.zip or .rar) and can be extracted to reveal the data.
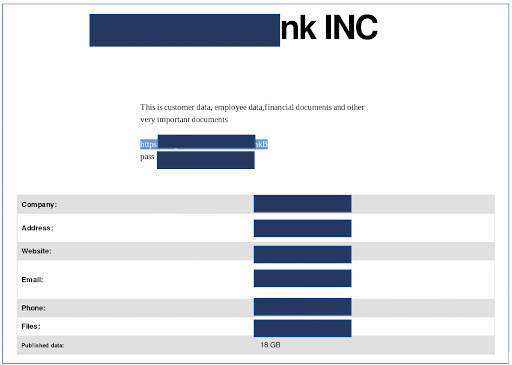
Example of the details which can be obtained through COMB on the dark web.
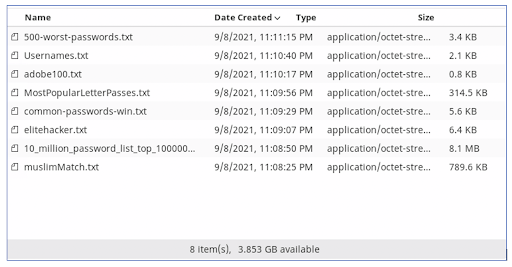
Another example where usernames and passwords were pulled from a dark web site. Notice one file containing 10 million passwords.
There are several measures individuals and organizations can take to remediate and prevent exploitation of the COMB data leak.
First, change your passwords immediately. This is a practice that should be performed often and on a regular basis. Using a password manager (local or cloud-based) that generates lengthy, complex passwords greater than 20 characters is a good way to keep track of your many unique passwords that follow best practice structure. Users and admins can also switch on two-factor authentication for password managers and individual sites, like Google Auth, Duo, SMS text verification, etc.
Individuals should also be weary of posting personal identifiable information (PII) on social media platforms, whether on their profiles, posts or comments.
For organizations, IT should evaluate the current browsing habits of end users, as well as network and host security settings. If proactive monitoring of endpoint and network activity, as well as regular penetration testing, aren’t part of your cybersecurity repertoire, the COMB leak is another reason they should be.
It’s also a great time to deliver another end-user education or training session on the risks of phishing, clicking on suspicious URLs, what misspellings could signal, etc.
For organizations concerned about the potential impacts of the COMB leak to their brand reputation, exposed credentials, fraud prevention/detection or other threats, researching the trove of information available on the dark web is essential.
If you’re new to dark web research, it’s important to understand the basics of what it is, how it’s accessed and what information can be found on which darknets. Most importantly, it’s important you understand the risks.
The dark web, like anywhere on the internet, comes with cyber risks. Just clicking on a link or visiting a site could introduce malicious content to your machine and network. And due to the dark web’s more unscrupulous users looking to ward off any unwanted attention, it may be particularly rife with cyberthreats. Simply logging in with your main work computer or with your personal laptop without any additional precautions could introduce risk to your environment or reveal company secrets or personal information.
That’s why remote browser isolation, while nice to have for the average internet user, is essential for anyone conducting online investigations, especially involving the dark web.
Investigators should also consider the digital fingerprint conveyed to website owners on the dark web. Your IP address, your browser history and cookies are all giving away information about you that you may not want to be found out. Even the language your device is set to or what browser you choose may give away important context that could tip off investigative targets as to who you are and why you’re on their site. This could lead not only to retaliation (cyber or physical) but disrupt the investigation due to disinformation or a target going into hiding.
Managed attribution gives investigators the power to control the details of their digital fingerprint to obfuscate their identity, affiliations and intent, as well as blend in with the crowd on sites they’re researching.
Dark web research is worth pursuing, as long as you have the right tools and tradecraft for the job.
To learn more about how Silo for Research can help investigators securely and anonymously conduct research across the surface, deep and dark web, check out these pages: